Connecting to Redshift
- Open the connections page in preferences, see managing connections for more information.
- Click the
Add new Connectionbutton at the top of the connections page.
- Select
Redshiftfrom the list.
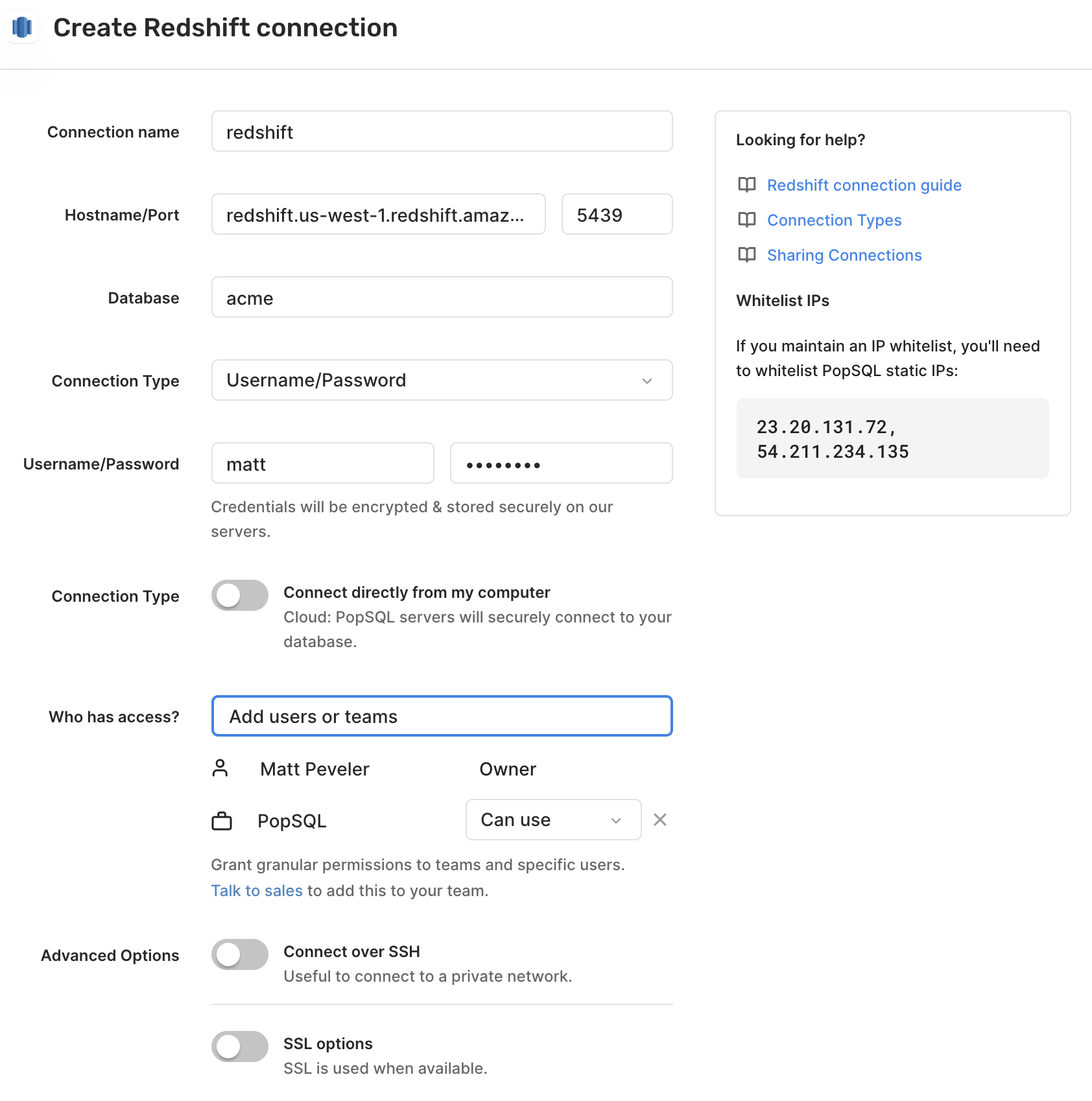
- Give a
Connection namefor your own internal reference. - For
Hostname, enter the hostname of your database server. - For
Port, use the default5439, or enter the port used by your server. - For
Database, enter the name of your database. - Select how to connect to database. See below for details on using AWS IAM.
- If using Username/Password, for
UsernameandPassword, enter the username and password for PostgreSQL. These are optional. - Toggle connection type for direct or cloud.
- Share the connection with your team.
- Configure
SSHandSSLsettings. These are optional. - Hit
Connectand you're all set!
Happy querying! 🍭
AWS IAM and Okta
For enterprise users, we support the ability to login with IAM credentials, an IAM profile, or Okta. If you are interested in these features, reach out to us at [email protected] to learn more.
Dashboards are not supported for these connection types yet. All other cloud features are fully supported (schedules, shared queries, Slack, web app, dbt integration, etc.)
Once enabled, you will be able to select one of the "Amazon RDS IAM" authentication methods for the connection. When using the credentials method, you will be asked for the Region, AWS Access Key ID, AWS Secret Access Key, and optionally the AWS Session Token, which can be acquired by going through the My Security Credentials page on AWS or provided by your administrator. For the profile method, you will be asked for Profile which corresponds to the named profile you have configured within the AWS CLI. When authenticating, PopSQL will then open that file to read the stored credential information.
For all methods, you will be asked for a Username that corresponds to the DB user you wish to use to connect to the database. Your administrator should have created the GetClusterCredentials IAM role for the user, as well as created the Database User Account for you to use. You can prefix the username with IAM: or IAMA: to disable or enable the AutoCreate parameter for the connection. If the Username field is left blank, then it will default to your OS' username with the AutoCreate flag enabled.
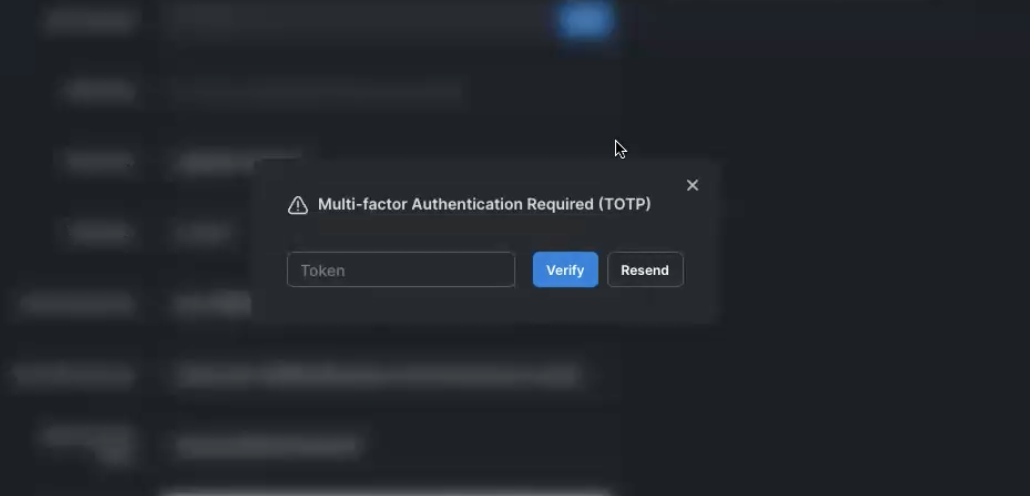
Multi-factor Authentication
If your AWS account requires multi-factor authentication, you will be prompted within PopSQL for that token and it will be cached until it expires, at which point the prompt will appear again.
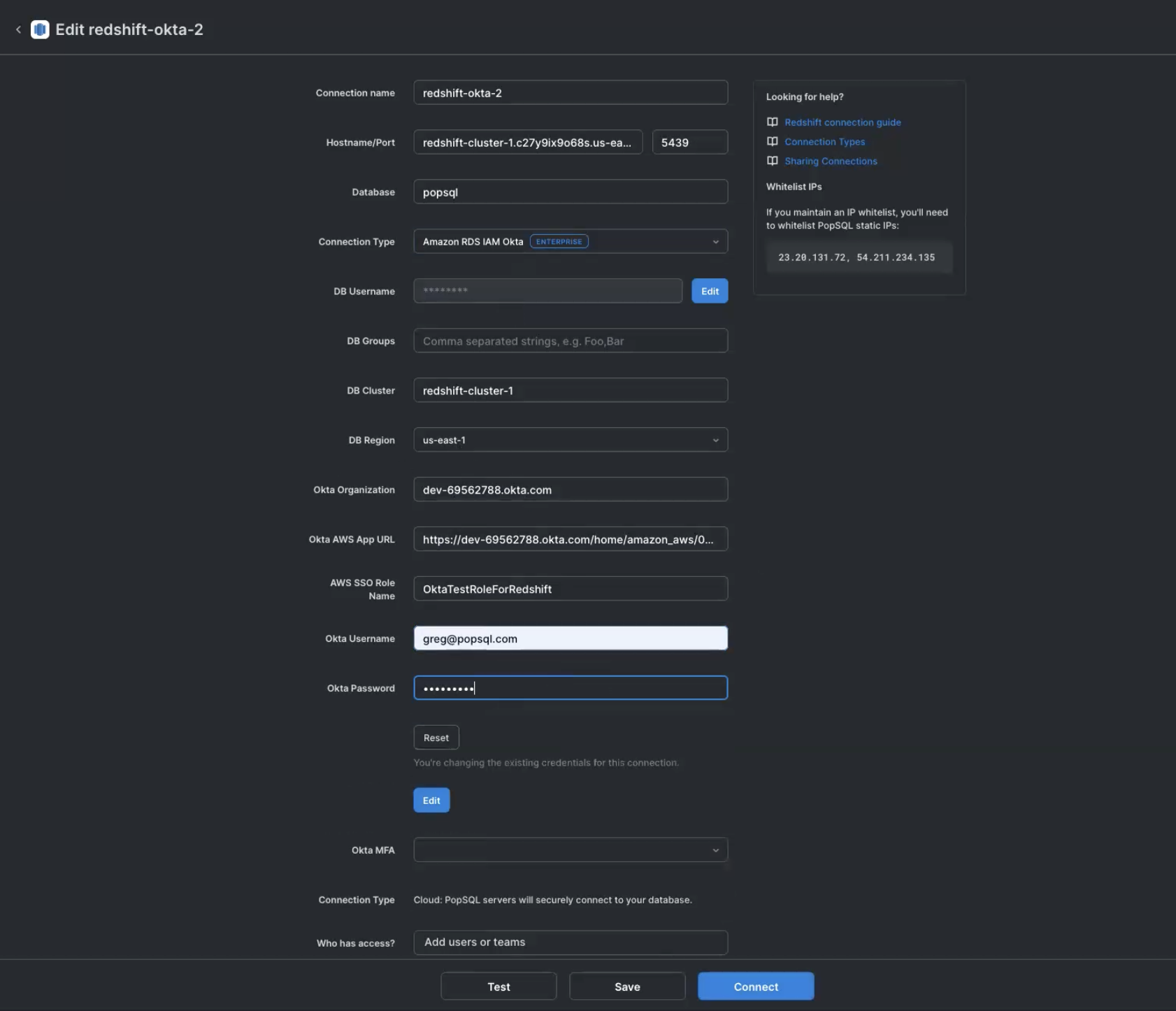
Amazon RDS IAM Okta
For the "Okta" method, it will utilize the AWS Account Federation integration through Okta to authenticate. You will need to provide your Okta organization (e.g. acme.okta.com), the "App Embed Url" for the integration, the region you wish to use, the role to authenticate with, and your okta username / password.
Updated 8 months ago
